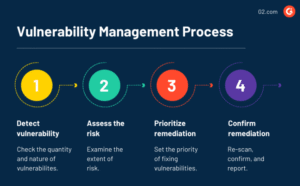
In today’s digital landscape, small businesses must prioritize cybersecurity to protect sensitive data and maintain customer trust. A Vulnerability Management (VM) program is a proactive approach to identifying, assessing, and mitigating security weaknesses in your IT infrastructure. Building a VM program from scratch may seem daunting, but with a structured plan, even small businesses with limited resources can establish an effective system. This article outlines a step-by-step guide to creating a VM program tailored to your small business needs.
Why Your Small Business Needs a VM Program
Cyberattacks, such as ransomware and data breaches, are increasingly targeting small businesses due to their often limited security resources. According to a 2023 report by Verizon, 43% of cyberattacks target small businesses, and 60% of those businesses fail within six months of a breach. A VM program helps you:
- Identify vulnerabilities before attackers exploit them.
- Protect customer data and maintain compliance with regulations (e.g., GDPR, CCPA).
- Reduce financial and reputational risks.
- Build trust with customers and partners.
Step 1: Define Goals and Scope
Before diving into technical details, establish clear objectives for your VM program. Ask yourself:
- What are you protecting? Identify critical assets, such as customer databases, financial records, or intellectual property.
- What are your compliance requirements? Determine if regulations like HIPAA or PCI-DSS apply to your business.
- What is your risk tolerance? Decide how much risk your business can accept and prioritize vulnerabilities accordingly.
Scope your program by mapping out your IT environment, including:
- Hardware (servers, workstations, IoT devices).
- Software (applications, operating systems).
- Network infrastructure (routers, firewalls).
- Cloud services (e.g., AWS, Google Workspace).
For small businesses, start with a narrow scope—focus on critical systems—and expand as resources allow.
Step 2: Assemble a VM Team
Even with a small team, designate roles to ensure accountability. Key roles include:
- Program Lead: Oversees the VM program, coordinates tasks, and reports to management (this could be the business owner or IT manager).
- IT Staff or Contractor: Performs scans, patches systems, and implements fixes.
- Stakeholders: Department heads or employees who provide input on critical assets and operational needs.
If your business lacks in-house expertise, consider outsourcing to a managed security service provider (MSSP) for tasks like vulnerability scanning or penetration testing.
Step 3: Conduct an Asset Inventory
A comprehensive asset inventory is the foundation of your VM program. Document all hardware, software, and services in your IT environment. For each asset, record:
- Asset type (e.g., server, application).
- Owner (e.g., IT department, third-party vendor).
- Criticality (e.g., high, medium, low).
- Location (e.g., on-premises, cloud).
Use free or affordable tools like Spiceworks Inventory or Open-AudIT to automate asset discovery for small businesses. Regularly update the inventory to account for new devices or software.
Step 4: Perform Vulnerability Scanning
Vulnerability scanning identifies weaknesses in your systems. Choose a scanning tool that fits your budget and technical expertise. Options include:
- Free Tools: OpenVAS or Nmap for basic scanning.
- Paid Tools: Nessus Essentials (free for up to 16 IPs) or Qualys Community Edition for small-scale use.
- Cloud-Based Solutions: Tenable.io or Rapid7 InsightVM for businesses with cloud infrastructure.
Best Practices for Scanning:
- Schedule regular scans (e.g., monthly or quarterly) to balance thoroughness and resource use.
- Start with non-intrusive scans to avoid disrupting operations.
- Scan both internal and external assets, as threats can originate from within or outside your network.
After each scan, generate a report detailing vulnerabilities, their severity (e.g., critical, high, medium, low), and affected assets.
Step 5: Prioritize and Remediate Vulnerabilities
Not all vulnerabilities require immediate action. Use a risk-based approach to prioritize remediation:
- Assess Severity: Most scanning tools assign a Common Vulnerability Scoring System (CVSS) score (0–10). Focus on vulnerabilities with scores of 7 or higher first.
- Consider Asset Criticality: Prioritize fixes for high-value assets (e.g., a customer database over a test server).
- Evaluate Exploitability: Check if a vulnerability has known exploits in the wild using resources like the National Vulnerability Database (NVD) or Exploit-DB.
Remediation Strategies:
- Patch Management: Apply software updates or security patches promptly. Use tools like WSUS (for Windows) or Ansible for automated patching.
- Configuration Changes: Adjust settings (e.g., disable unused ports or services) to reduce attack surfaces.
- Workarounds: If patching isn’t immediately possible, implement temporary measures, such as firewall rules or network segmentation.
- Retire Obsolete Systems: Replace outdated software or hardware that can’t be patched.
Document all remediation actions, including who performed them and when.
Step 6: Monitor and Maintain the Program
A VM program is not a one-time effort—it requires ongoing maintenance. Key activities include:
- Continuous Monitoring: Use tools like Zabbix or Nagios to monitor network activity and detect anomalies.
- Regular Reporting: Share progress with stakeholders, highlighting vulnerabilities found, fixed, and pending.
- Employee Training: Educate staff on security best practices, such as recognizing phishing emails or using strong passwords.
- Program Review: Annually assess your VM program’s effectiveness and adjust goals, tools, or processes as needed.
Step 7: Leverage Free and Affordable Resources
Small businesses often operate on tight budgets. Fortunately, many free or low-cost resources can support your VM program:
- Frameworks: Adopt guidelines from NIST SP 800-53 or CIS Controls (free versions available).
- Communities: Join forums like Reddit’s r/cybersecurity or SANS Small Business Cybersecurity for advice and peer support.
- Training: Access free courses from Cybrary or SANS Cyber Aces to upskill your team.
Common Pitfalls to Avoid
- Ignoring Low-Severity Vulnerabilities: These can be chained together by attackers to create significant breaches.
- Over-Reliance on Automation: Tools can’t catch everything—manual reviews are essential for context.
- Neglecting Employee Awareness: Human error is a leading cause of breaches. Regular training is critical.
- Failing to Document: Without records, it’s hard to track progress or demonstrate compliance.
Conclusion
Building a vulnerability management program from scratch is a manageable task for small businesses with the right approach. By defining clear goals, leveraging affordable tools, and fostering a security-conscious culture, you can protect your business from cyber threats and build resilience. Start small, focus on critical assets, and scale your program as your business grows. With consistent effort, your VM program will become a cornerstone of your cybersecurity strategy, safeguarding your operations and reputation in an increasingly risky digital world.
Cloud Vulnerabilities 101: Are You Leaving Your Data Exposed?
Cloud computing has revolutionized how businesses operate, offering scalability, cost-efficiency, and flexibility. However, the cloud is not a silver bullet for security. Misconfigurations, inadequate access controls, and overlooked vulnerabilities can expose sensitive data to cyberattacks. For small businesses relying on cloud services like AWS, Microsoft Azure, or Google Cloud, understanding and mitigating cloud vulnerabilities is critical to safeguarding data. This article provides a practical, deeply thought-out guide to common cloud vulnerabilities, their risks, and actionable steps to secure your cloud environment.
Why Cloud Security Matters
The shift to cloud infrastructure has accelerated, with 94% of enterprises using cloud services, according to a 2023 Flexera report. Yet, cloud-related breaches are rising—IBM’s 2024 Cost of a Data Breach report notes that 45% of breaches involved cloud environments, costing businesses an average of $4.88 million. Small businesses, often lacking dedicated cybersecurity teams, are particularly vulnerable. A single misstep can lead to data leaks, ransomware, or regulatory penalties under laws like GDPR or CCPA.
This article explores the most prevalent cloud vulnerabilities, their root causes, and practical mitigation strategies to ensure your data remains protected.
Common Cloud Vulnerabilities
1. Misconfigurations
What It Is: Misconfigurations occur when cloud resources—such as storage buckets, databases, or virtual machines—are improperly set up, leaving them exposed to unauthorized access.
Risks: A 2024 Sophos report found that 70% of cloud breaches stem from misconfigurations. For example, an unsecured Amazon S3 bucket could expose customer data, leading to reputational damage and fines.
Examples:
- Publicly accessible storage buckets (e.g., S3 buckets with “public” permissions).
- Unrestricted firewall rules allowing inbound traffic from any IP.
- Exposed API keys or credentials in configuration files.
Mitigation:
- Use Configuration Management Tools: Tools like AWS Config, Azure Security Center, or Google Cloud Security Command Center can detect and alert on misconfigurations.
- Implement Least Privilege: Restrict permissions to the minimum required for each user or service. Use Identity and Access Management (IAM) policies to enforce this.
- Regular Audits: Conduct monthly audits using tools like CloudSploit (open-source) or Tenable.io to identify misconfigured resources.
- Enable Logging: Activate logging (e.g., AWS CloudTrail, Azure Monitor) to track changes and detect unauthorized access attempts.
2. Weak Access Controls
What It Is: Inadequate authentication or authorization mechanisms allow unauthorized users to access cloud resources.
Risks: Weak access controls can lead to account hijacking or privilege escalation. A compromised account with excessive permissions could give attackers full control over your cloud environment.
Examples:
- Lack of multi-factor authentication (MFA) on admin accounts.
- Overly permissive IAM roles (e.g., granting “Admin” access to all users).
- Reusing passwords across accounts or services.
Mitigation:
- Enforce MFA: Require MFA for all users, especially those with elevated privileges. Most cloud providers offer free MFA options.
- Rotate Credentials: Regularly update passwords and API keys. Use credential management tools like AWS Secrets Manager or HashiCorp Vault.
- Implement Role-Based Access Control (RBAC): Assign roles based on job functions, limiting access to only necessary resources.
- Monitor Account Activity: Use anomaly detection tools (e.g., Azure Sentinel, Google Cloud’s Event Threat Detection) to flag suspicious logins or privilege escalations.
3. Insecure APIs
What It Is: APIs, the backbone of cloud services, can be exploited if not properly secured, allowing attackers to access or manipulate data.
Risks: Insecure APIs can lead to data leaks or service disruptions. A 2023 Salt Security report found that 80% of organizations experienced API-related security incidents.
Examples:
- APIs without proper authentication (e.g., missing OAuth tokens).
- Exposed API endpoints revealing sensitive data.
- Lack of rate limiting, enabling brute-force attacks.
Mitigation:
- Secure API Endpoints: Use HTTPS and enforce authentication (e.g., OAuth 2.0 or API keys).
- Validate Inputs: Implement input validation to prevent injection attacks (e.g., SQL or command injection).
- Rate Limit APIs: Restrict the number of requests per user to mitigate abuse. Cloud providers like AWS offer tools like API Gateway for this.
- Audit APIs: Regularly test APIs using tools like Postman or OWASP ZAP to identify vulnerabilities.
4. Data Exposure in Transit or at Rest
What It Is: Unencrypted data, whether stored in the cloud or transmitted between services, is vulnerable to interception or theft.
Risks: Exposed data can lead to breaches, especially if it includes personally identifiable information (PII) or financial records.
Examples:
- Unencrypted databases or storage buckets.
- Data transmitted over HTTP instead of HTTPS.
- Missing encryption keys for sensitive backups.
Mitigation:
- Encrypt Data at Rest: Use server-side encryption (e.g., AWS KMS, Azure Key Vault) for all stored data.
- Encrypt Data in Transit: Enforce TLS/SSL for all communications. Verify that APIs and web apps use HTTPS.
- Manage Encryption Keys: Store keys securely using key management services and rotate them regularly.
- Classify Data: Identify sensitive data and apply stricter encryption policies to it.
5. Inadequate Vulnerability Management
What It Is: Failing to identify and patch vulnerabilities in cloud infrastructure, such as outdated software or misconfigured services.
Risks: Unpatched vulnerabilities are low-hanging fruit for attackers. The 2023 Log4j vulnerability, for instance, affected thousands of cloud-based applications.
Examples:
- Running outdated container images with known vulnerabilities.
- Neglecting to update cloud provider services (e.g., Kubernetes clusters).
- Ignoring vulnerabilities flagged by scanning tools.
Mitigation:
- Run Regular Scans: Use vulnerability scanners like Qualys, Nessus, or cloud-native tools (e.g., AWS Inspector) to identify weaknesses.
- Patch Promptly: Apply patches for software, containers, and cloud services as soon as they’re available.
- Automate Updates: Use tools like AWS Systems Manager or Azure Automation to streamline patch deployment.
- Monitor Advisories: Stay informed about new vulnerabilities via the National Vulnerability Database (NVD) or cloud provider alerts.
Practical Steps to Secure Your Cloud Environment
Step 1: Conduct a Cloud Security Assessment
Start by evaluating your current cloud setup. Use free or affordable tools like CloudMapper (for AWS) or Prowler (multi-cloud) to generate a security baseline. Identify misconfigurations, exposed resources, and compliance gaps.
Step 2: Adopt a Shared Responsibility Model
Understand the cloud provider’s shared responsibility model. For example:
- Provider Responsibilities: Physical security, hypervisor protection.
- Your Responsibilities: Securing data, configuring resources, managing access.
Review your provider’s documentation (e.g., AWS Shared Responsibility Model) to clarify your role.
Step 3: Implement a Zero Trust Architecture
Assume no user or device is inherently trustworthy. Key principles include:
- Verify every access request, regardless of origin.
- Use micro-segmentation to isolate workloads.
- Continuously monitor and log activity.
Tools like Okta or Cloudflare Zero Trust can help small businesses implement this approach.
Step 4: Train Your Team
Human error is a leading cause of cloud breaches. Train employees on:
- Recognizing phishing attacks that target cloud credentials.
- Following secure configuration practices.
- Reporting suspicious activity promptly.
Leverage free resources like Cybrary or SANS Security Awareness for training.
Step 5: Develop an Incident Response Plan
Prepare for breaches by creating a plan that includes:
- Identification: Tools to detect incidents (e.g., intrusion detection systems).
- Containment: Steps to isolate affected resources.
- Recovery: Procedures to restore services and data.
- Post-Mortem: Analysis to prevent recurrence.
Test the plan annually using tabletop exercises.
Free and Affordable Tools for Small Businesses
- Cloud-Native Tools: AWS Trusted Advisor, Azure Defender, Google Cloud Security Scanner (free tiers available).
- Open-Source Tools: OpenVAS (vulnerability scanning), Falco (runtime security), Wazuh (security monitoring).
- Community Resources: Join Cloud Security Alliance or Reddit’s r/cloudsecurity for advice and best practices.
Common Pitfalls to Avoid
- Assuming Cloud Providers Handle All Security: You’re responsible for securing your data and configurations.
- Overlooking Third-Party Services: Vet SaaS tools (e.g., Dropbox, Slack) for security compliance.
- Neglecting Backups: Ensure backups are encrypted and tested regularly.
- Set-and-Forget Mentality: Cloud environments change rapidly—continuous monitoring is essential.
Conclusion
Cloud vulnerabilities are a real threat, but they’re manageable with proactive measures. By addressing misconfigurations, securing access controls, protecting data, and maintaining a robust vulnerability management process, small businesses can significantly reduce their risk. Start with a security assessment, leverage affordable tools, and foster a culture of vigilance. The cloud offers immense benefits, but only if you take responsibility for keeping your data safe. Are you leaving your data exposed? With the right strategy, you can answer “no” with confidence.